Quantum Communication: Quantum Key Distribution

The concept of QKD (Quantum Key Distribution) came about as a solution to the increasing need for secure communication in a world where traditional cryptographic methods are becoming increasingly vulnerable to attacks due to advances in computing power and the emergence of quantum computing.
What is cryptography?
Cryptography is the art of distributing a message which is impossible to understand by any unauthorized party. In order to achieve this goal, an algorithm (also called a Cryptosystem or cipher) is used to combine a message with some additional information known as the “key” — and produce a cryptogram. This technique is known as “encryption”.
And the Decryption is the reverse process of converting the ciphertext back into the original plaintext.For a Cryptosystem to be secure, it should be impossible to unlock the cryptogram without the key.
Cryptosystems come in two main categories — Asymmetric and symmetric cryptography, and are classified on the basis of the key used for encryption and decryption.
1) Asymmetrical Systems: Asymmetric cryptography (also known as public-key cryptography) uses two keys, a public key for encryption and a secret or private key for decryption. The public key can be freely shared and used by anyone. The private key is kept secret by the owner and is used to decrypt the messages.
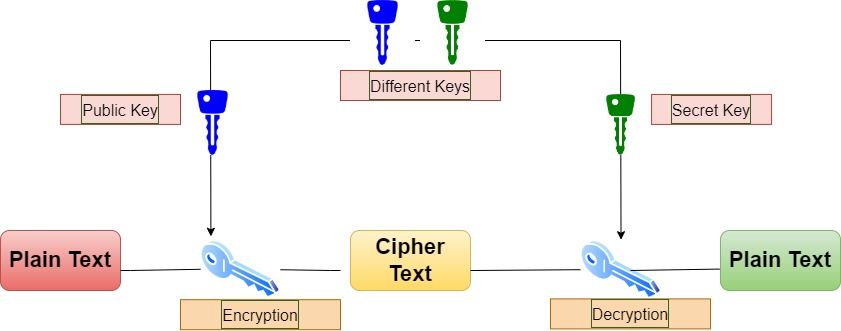
2) Symmetrical Systems: Symmetric cryptography (also known as private-key cryptography) uses a single key for both encryption and decryption. Both the sender and the receiver must have access to the same key, which must be kept secret from all other parties. The key distribution problem makes it less secure.
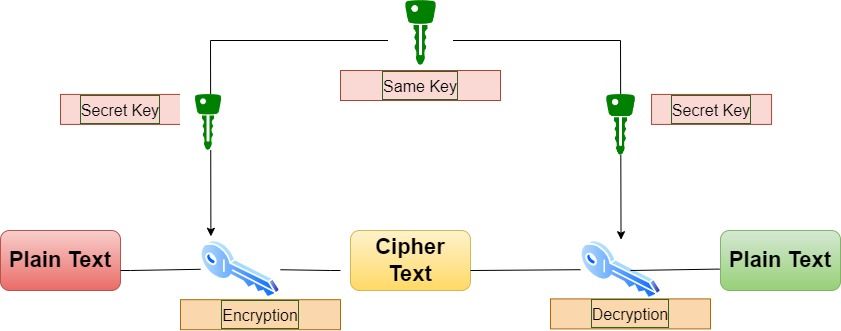
The main disadvantage of the symmetric key encryption is that all parties involved have to exchange the key used to encrypt the data before they can decrypt it.
So, in cryptography system securely sharing of secret keys between two parties who want to communicate is important.
Therefore, the concept of QKD comes into the picture.QKD was developed to provide a secure method for key distribution that is not susceptible to attacks. In QKD, the key is transferred using the principles of quantum mechanics, which provide a much higher level of security than traditional encryption methods. The key is transferred as a sequence of quantum states, and any attempt to intercept the key will result in a disturbance of the quantum states, which can be detected by the parties involved.
Definition: Quantum key distribution (QKD) is a secure communication method that implements a cryptographic protocol involving components of quantum mechanics. It enables two parties to produce a shared random secret key known only to them, which then can be used to encrypt and decrypt messages.
QKD works by using photons ,the particles, which transmit light to transfer data.
What are Photons? Photon, also known as light quantum.They are the smallest and most basic unit of light and other electromagnetic radiation. They do not have mass, but they have momentum and energy. Photons play a crucial role in many physical phenomena, such as electromagnetic radiation, quantum mechanics, and quantum field theory. They are used in numerous applications in physics, engineering, and technology, including quantum cryptography and quantum communication.
Quantum Principles used in QKD:
- Superposition: The ability of quantum particles to exist in multiple states simultaneously, allowing for the encoding of information in a single particle. This principle allows photons to exist in multiple states at the same time, which enables them to carry multiple bits of information in a single quantum system.
- Entanglement: The correlation between the properties of two or more quantum particles, even when separated by large distances.This principle allows photons to become entangled, such that the state of one photon is dependent on the state of another photon. This is the basis for the security of QKD.
- No-cloning theorem: The principle states that it is not possible to make an exact copy of an arbitrary unknown quantum state, which prevents an attacker from copying the quantum key without disturbing the system.
- Heisenberg's uncertainty principle: The principle states that it is impossible to precisely determine certain properties of a quantum particle, such as its position and momentum, at the same time.In QKD, this principle is used to ensure that if an attacker tries to determine the state of the quantum key, it will introduce an errors that are detected by the receiver.
- Wave polarization: Photon polarization refers to the orientation of the electric field in a photon, which is a quantum of light. Photons can be polarized vertically, horizontally, or at any angle in between, and this polarization can be used as a way to encode information. In quantum key distribution, polarization states of single photons are used to transfer a key between two parties securely.
Properties of photons make them an ideal choice for use in QKD:
No-cloning theorem: Photons cannot be exactly copied, ensuring the security of the encryption key.
Transmission through optical fibers: Photons can be transmitted over optical fibers, allowing for the distribution of the encryption key over long distances.
Interference: Photons can exhibit interference patterns, which can be used to detect eavesdropping attempts and ensure the security of the key distribution.
Coherence: Photons maintain their coherence over long distances, allowing for the efficient transmission of the encryption key.
Speed of light: Photons travel at the speed of light, making them a fast and efficient means of transmitting information.
Working of QKD
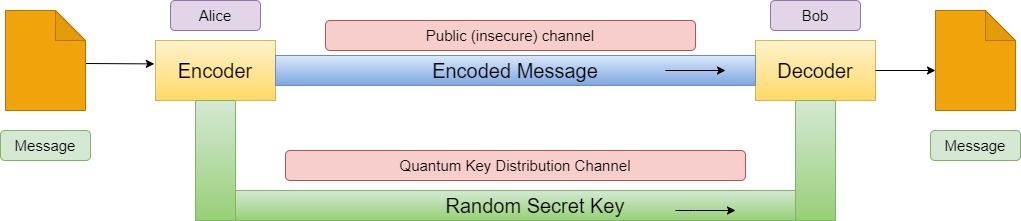
The basic idea behind QKD is to enable two distant users, to generate a common and random secret key. This is done through interactions between the two users, which need to be authenticated. This authentication can be achieved through various cryptographic means.
In QKD, the two authorized users, commonly referred to as Alice and Bob, use two different channels for communication: a public channel and a quantum channel.
The public channel is used to announce the setup and exchange of information that can be done in public. This includes the transmission of information such as the parameters of the protocol, the basis choice for encoding the qubits etc.
The quantum channel is used to transmit the qubits. The key is sent in the form of "qubits" which are essentially quantum bits. Qubits are transmitted as photons over optical fibers, which are capable of transmitting large amounts of data over long distances quickly.The quantum channel is designed to be secure and to preserve the integrity of the quantum states. Any attempt to eavesdrop on the quantum channel will cause a disturbance to the qubits, which will result in transmission errors that can be detected by the legitimate users.
In short, the public channel is used to transmit the initial information required for authentication, such as the key exchange protocol, and any other public information. However, the actual encryption key is sent through the quantum channel, which is kept private and secure, to protect the transmission from any unauthorized third-party interference.
QKD-Protocols
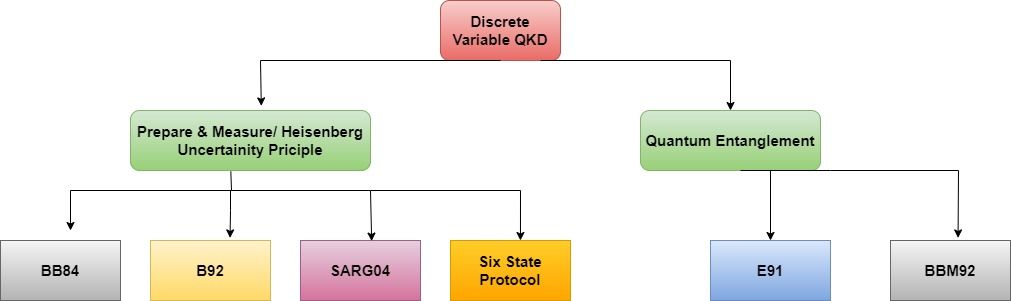
There are three main families of quantum communication protocols, known as Discrete-Variable (DV) protocol, Continuous-Variable (CV) protocol, and Distributed Phase Reference (DPR) protocol, differentiated on basis of the detection scheme used. DV and DPR protocol uses photon counting, while CV coding utilizes homodyne detection. Despite the different detection methods, all three families rely on the non-orthogonality of light states, which can be achieved through either prepare-and-measure or entanglement-based sources for photon generation.
- Discrete-Variable (DV) Protocols: This family of protocols uses discrete variables, such as the number of photons, to encode information. In DV coding, the detection scheme is based on photon counting. After the detection is completed, only those events in which a photon has been effectively detected are selected for further processing.
- Continuous-Variable (CV) Protocols: This family of protocols uses continuous variables, such as the amplitude and phase of a light wave, to encode information. In CV coding, the detection scheme is based on homodyne detection, which involves mixing the signal with a strong local oscillator and measuring the resulting interference pattern.
- Distributed Phase Reference (DPR) Protocols: This family of protocols also uses photon counting as the detection scheme, but it differs from DV coding in that it relies on the phase of the light wave to encode information. In DPR coding, the phase reference is distributed between the communicating parties, allowing for the secure exchange of information.
Each of these families of protocols has its own strengths and weaknesses, and the choice of which to use will depend on the specific requirements of the communication scenario. However, all three rely on the fundamental property of non-orthogonality of quantum states for secure communication.
Non-orthogonality : The non-orthogonality of quantum states in quantum communication refers to the fact that two quantum states can overlap, meaning they cannot be distinguished perfectly from one another. This property is used in quantum cryptography for secure communication.Hence, Non-orthogonality is used to send secure messages that are encoded as quantum states. Since it is impossible to distinguish between two overlapping quantum states perfectly, any attempt to intercept the message will change the state, making it possible to detect the eavesdropping.
The security of quantum communication protocols is based on either the principle of measurement or the phenomenon of entanglement.
- In the case of the principle of measurement, the security is based on the fact that any measurement of an unknown quantum state will disturb the state and introduce detectable changes in it. This property is known as the Heisenberg Uncertainty Principle and is a fundamental aspect of quantum mechanics. In quantum key distribution (QKD) protocols, this principle is used to detect the presence of an eavesdropper who attempts to intercept and measure the quantum states being transmitted between two parties. If the eavesdropper measures the quantum state, they will introduce detectable changes in the state, allowing the authorized parties to detect the eavesdropping and abort the communication.
- On the other hand, the phenomenon of entanglement is used in some quantum communication protocols to ensure the security of the transmitted information. In entanglement-based protocols, the two parties share an entangled quantum state, and the information is encoded in the correlations between the entangled particles. This makes it extremely difficult for an eavesdropper to access the information without being detected.
These principles form the foundation of the security of quantum communication protocols and can be implemented using DV, CV, and DPR protocols.Hence allow for secure communication even in the presence of an eavesdropper Among these, the discrete-variable (DV) protocol is the most widely used and well-studied.
1- Discrete Variable Protocols
In Discrete Variable (DV) protocols, information is encoded into the quantum states of single photons, or other discrete-valued quantum systems. The most common example of such a discrete quantum degree of freedom is polarization. In a polarized photon, the polarization state can take one of two values: horizontal or vertical, for example. The quantum state of each photon can then be used to represent a binary bit of information. The security of DV protocols is based on the quantum mechanical properties of the states used, such as the difficulty of cloning an unknown quantum state or the fact that the measurement of a quantum state will disturb it.
The protocols in this family rely on the concept of photon counting, meaning that only events in which a detection has effectively taken place are selected after the detection is completed. The raw key generated by DV protocols is usually post-processed using error correction and privacy amplification algorithms to convert it into a secret key.
i) Prepare and Measure
a) BB84
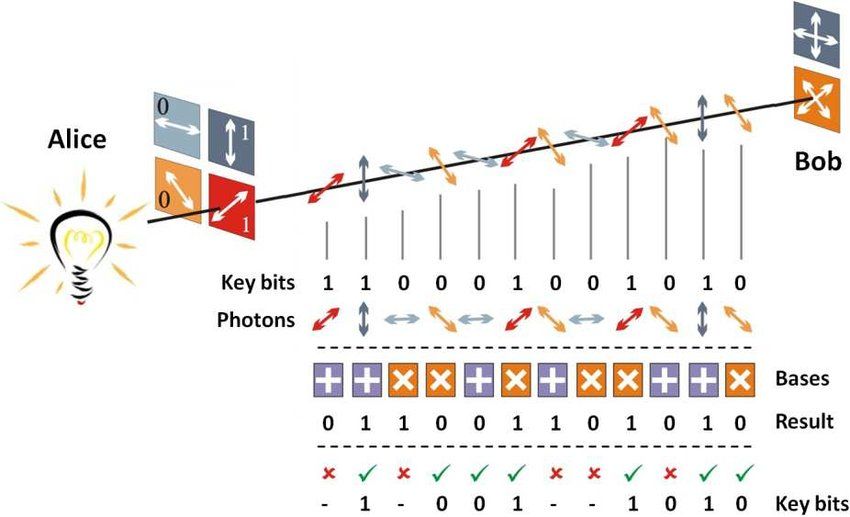
The BB84 protocol, named after its inventors Charles Bennett and Gilles Brassard, is one of the most well-known quantum key distribution (QKD) protocols. It was first published in 1984 and is considered to be the first practical and experimental demonstration of quantum cryptography.
The basic idea behind the BB84 protocol is that two parties, commonly referred to as Alice and Bob, can securely exchange a secret key using quantum states. The key is used to encrypt and decrypt messages between Alice and Bob.
In the BB84 protocol, Alice sends a sequence of qubits (quantum bits) to Bob over an insecure channel. Each qubit is in one of four possible states, chosen randomly from two non-orthogonal sets of two states. Bob then measures each qubit, choosing randomly between two different measurement bases. After measuring all the qubits, Bob tells Alice which measurement basis he used for each qubit. Alice then tells Bob which of her states correspond to the qubits that Bob measured.
The two parties then use classical communication to compare their choices of states, and discard any bits that are not the same. This ensures that the final shared message is secure against eavesdropping, as any attempt to intercept the message will inevitably change the state, making it possible to detect the eavesdropping.
Once the secure key has been established, it can be used for secure communication.The BB84 protocol is widely considered to be the first and most important quantum key distribution protocol.
The security of the BB84 protocol is based on the fundamental principle of quantum mechanics that the measurement of a quantum state collapses the state into one of its eigenstates, destroying the original state. This means that an eavesdropper, who attempts to intercept and measure the quantum states, will inevitably disturb the states and create detectable anomalies in the measurements.
b)B92
The B92 protocol is another type of quantum key distribution (QKD) protocol. It was introduced by Bennett in 1992 as an improvement over the BB84 protocol, which is one of the most well-known QKD protocols.
In the B92 protocol, Alice sends a sequence of qubits (quantum bits) to Bob, who then measures the qubits and sends his measurement results back to Alice. Alice then uses this information to determine the key.
The main difference between the B92 and BB84 protocols is that the B92 protocol uses only two non-orthogonal states, while the BB84 protocol uses four non-orthogonal states. This makes the B92 protocol simpler than the BB84 protocol, both in terms of its theoretical foundations and its implementation.
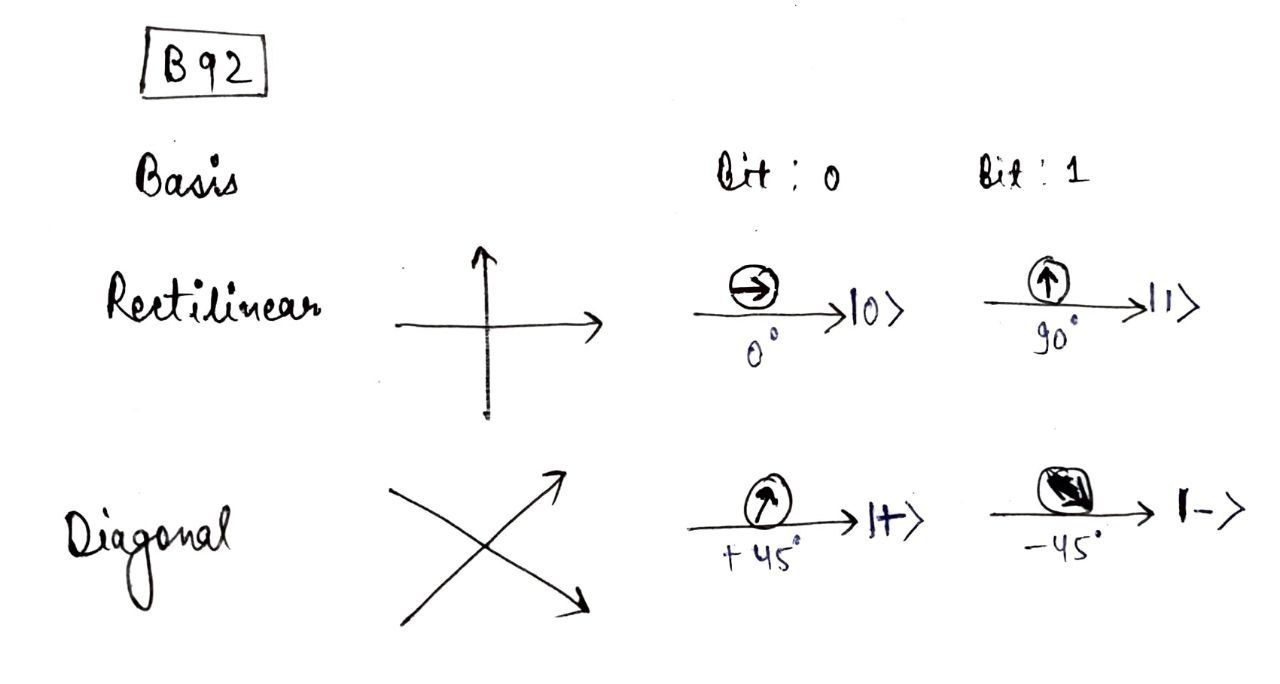
Like the BB84 protocol, the B92 protocol is based on the principle of quantum mechanics that measurement of a quantum state creates detectable anomalies in the state of the qubit. However, the B92 protocol differs from the BB84 protocol in the way the quantum states are prepared and measured.
The use of four states in the BB84 protocol makes it more secure and resistant to certain types of attacks, but also more complex and challenging to implement. The use of only two states in the B92 protocol makes it simpler and easier to implement, but less secure.
The security of the B92 protocol comes from the fact that an eavesdropper, Eve, trying to intercept the information will introduce errors in the transmission, which can be detected by the sender and receiver. If they detect errors, they can abort the communication and start over.
c) SARG04
SARG04 (named after Valerio Scarani, Antonio Acin, Gregoire Ribordy, and Nicolas Gisin) is a 2004 quantum cryptography protocol derived from the first protocol of that kind, BB84.
This protocol has been built when researchers noticed that by using the four states of BB84 with a different information encoding they could develop a new protocol which would be more robust, especially against the PNS(Photon Number Splitting Attack) , when attenuated laser pulses are used instead of single photon sources.
SARG04 was defined by Scarani et al. in 2004 as a prepare and measure version(in which it is equivalent to BB84 when viewed at the level of quantum processing.
It is a prepare-and-measure quantum cryptography protocol in which, the qubits are encoded using two n-bit strings, "a" and "b," with "b" being used to decide the basis of "a". Only Alice knows the value of "b," so it becomes impossible for Bob or any eavesdropper to distinguish the states of the qubits without knowing "b".
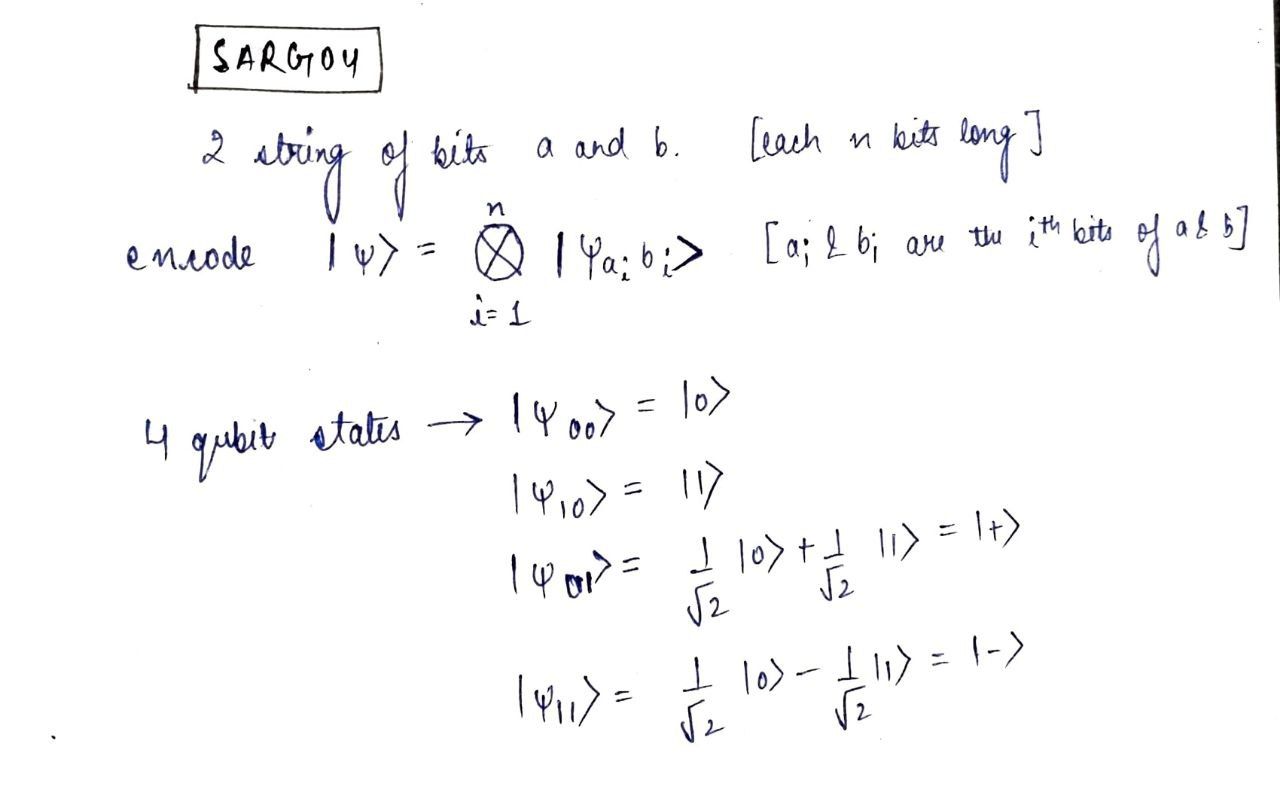
Bob generates a string of random bits of length b and measures the qubits sent by Alice using the correct basis based on the value of b. Alice then announces a pair of non-orthogonal states, one of which she used to encode her bit, and Bob uses the correct basis to determine the state. Alice keeps a record of the states of the qubits, which makes up the secret key to be shared with Bob.
The SARG04 protocol has been proven to be secure as it is more robust against the Photon Number Splitting (PNS) attack than BB84 when attenuated laser pulses are used for transmission instead of polarized photons. An improved version of SARG04 with a zero error rate against the PNS attack has also been proposed, and it has been applied in commercial quantum key distribution (QKD) systems for its robustness against PNS attacks.
d) 6-State Protocol
The 6-State protocol is a Quantum Key Distribution (QKD) protocol that uses the polarization states of single photons to encode information. This protocol is similar to the BB84 protocol and it uses six polarization states to encode the key, rather than four in the BB84 protocol.
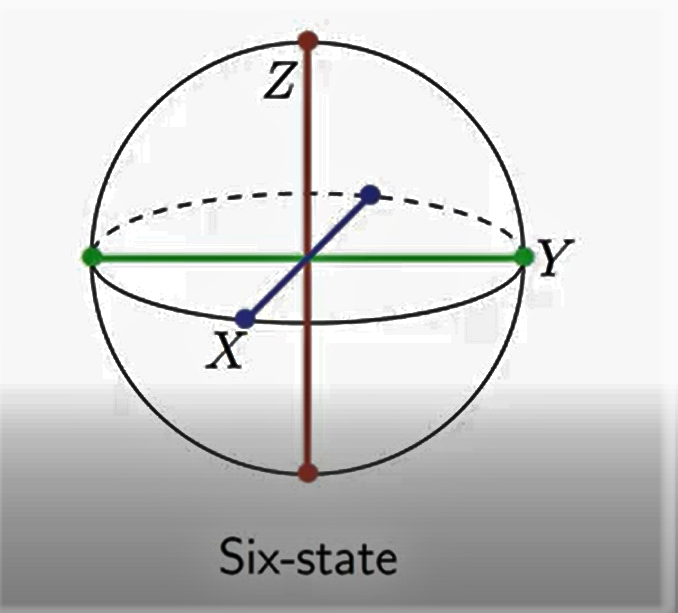
In the 6-state protocol, Alice prepares and sends six different quantum states instead of the four states used in the BB84 protocol. This allows for a larger number of encoding possibilities, making the protocol more secure against eavesdropping. In the protocol, Alice and Bob randomly choose one of the six quantum states and encode their bits, and then measure the received quantum states to determine the key.
In the 6-State protocol, two parties, commonly referred to as Alice and Bob, want to establish a secure key over a public channel. Alice randomly chooses one of the six polarization states and sends a photon to Bob, who measures the polarization state of the photon. Bob informs Alice of the measurement basis he used, but not the measurement result.
Alice then compares the measurement basis used by Bob to the polarization state she originally sent. If they match, then Alice keeps the result, otherwise she discards it. This process is repeated multiple times until enough key bits have been generated.
The 6-State protocol provides increased security compared to the BB84 protocol, as the use of six polarization states makes it more resistant to eavesdropping. However, it also requires more complex experimental setup and higher accuracy in the measurement, as compared to the BB84 protocol.
ii) Quantum Entanglement
a) E91
The E91 protocol, also known as the Ekert91 protocol, is a quantum cryptography protocol developed by Artur Ekert in 1991. It is one of the earliest quantum key distribution (QKD) protocols and is based on the principle of quantum entanglement.
The E91 protocol is a quantum cryptography protocol that was invented by Artur Ekert in 1991. It is based on the concept of quantum entanglement, which states that the quantum states of two entangled particles are correlated such that measuring the state of one particle will determine the state of the other particle, no matter the distance between them.
The protocol uses a pair of entangled photons, which can be created by either the sender (Alice), the receiver (Bob), or a third party. Alice and Bob measure the polarizations of their respective particles and if they choose compatible bases, the measurement results will be anti-correlated. However, if the bases are not compatible, the measurement results will be random.
To discard these random measurements, Alice and Bob must announce the basis they used to measure their particles publicly. Any attempt by an eavesdropper to intercept the communication will destroy the correlation of the entangled particles, which can be detected.
The security of the E91 protocol relies on the fact that any attempt by an eavesdropper, Eve, to intercept and measure the entangled particles will cause a disturbance in the quantum states and result in an easily detectable change in the correlation between Alice and Bob's measurement results.
b) BBM92
BBM92 (Bennett, Brassard, Mermin , 1992) is a quantum key distribution (QKD) protocol that is based on the BB84 protocol.The BBM92 protocol is a variant of the BB84 protocol and uses a third party to generate entangled photon pairs. In this protocol, a sender and a receiver share an entangled pair of particles, and by performing measurements on these particles, they can establish a shared secret key.
The third party sends one photon of each entangled pair to Alice and the other to Bob, who perform their own independent measurements. The use of a third party to generate the entangled pairs is intended to prevent Eve (the eavesdropper) from becoming entangled with either Alice or Bob's qubits, and thus causing any errors in the measurements. This is seen as an added security measure to protect the key distribution process.
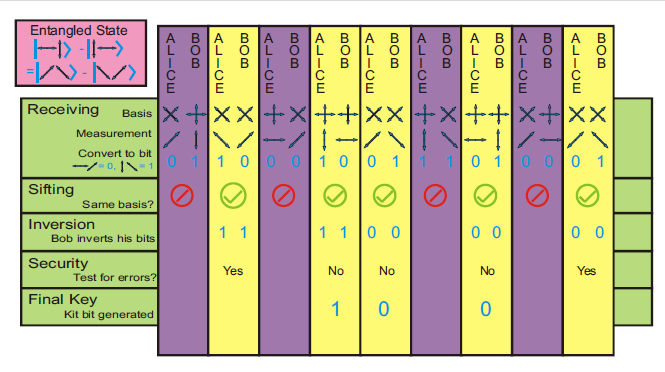
- One photon of each pair is sent to Alice and the other is sent to Bob.
- Alice and Bob perform measurements independently by randomly choosing one of the two non-compatible bases.
- They then publicly announce the basis they chose in order to get the correlated measurements and generate the secret key.
- The third party generates the entangled pairs to ensure that Eve cannot become entangled to either Alice or Bob's qubits and cause any errors in the measurements.
However, this protocol provides higher security when it includes a Bell test. The security analysis of entanglement-based QKD protocols, including BBM92, is an active area of research.
The BBM92 protocol is considered to be one of the most secure QKD protocols, but it is also more complex than some of the other protocols, such as the BB84 or the B92 protocol.
2) Continuous-Variable (CV) Protocol
Continuous-Variable (CV) protocols are a type of Quantum Key Distribution (QKD) protocols that use the continuous nature of optical quadratures (amplitude and phase) to encode and transmit information. Unlike Discrete-Variable (DV) protocols that use discrete quantum states, CV protocols use a continuous set of states, making it more resilient to certain types of noise and loss compared to DV protocols.
CV-QKD protocols typically use coherent states , squeezed states or No Switching protocol to encode the information, and homodyne detection to measure the optical quadratures. Some of the well-known CV protocols include the Gaussian-modulated/ Homodyne detection and Discrete Modulation protocol. These protocols are still in the experimental stage, but they have shown promise in achieving high secret key rates over longer distances compared to DV protocols.
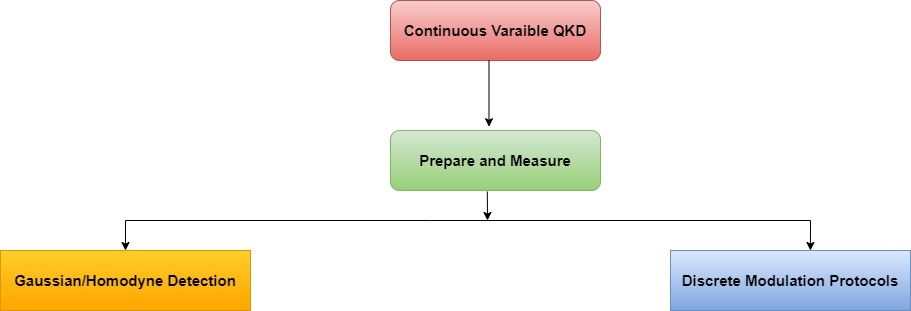
i) Prepare and Measure
a) Gaussian/ Homodyne Detection
CV-QKD protocols differ from traditional QKD protocols in that they use homodyne/heterodyne detection techniques instead of photon counting technology. The Gaussian class of CV protocols uses a continuous modulation and can be further divided into three categories: Squeezed State protocols, Coherent State protocols, and No Switching protocols.
- Squeezed State protocols: In this the sender (Alice) uses squeezed states of light that are displaced along the squeezed quadrature and the receiver (Bob) performs homodyne detection.
- Coherent State protocols: In this coherent states of light are generated by Alice and homodyne detection is performed by Bob.
- No Switching protocols: In this , Bob uses heterodyne detection and allows for the generation of secret keys without the need for random switching between the two conjugated bases.
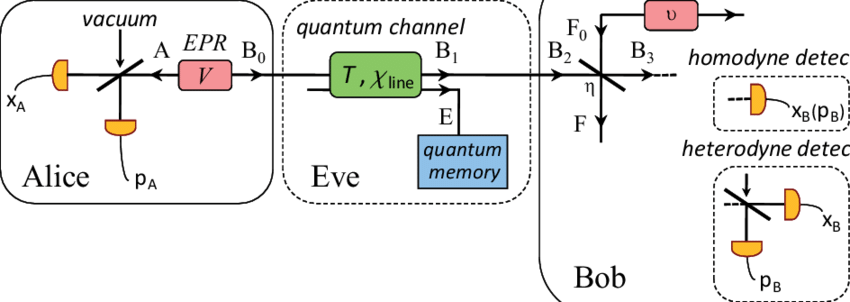
Homodyne detection is a technique used in continuous-variable quantum key distribution (CV-QKD) protocols to detect the presence of an eavesdropper in a communication system.The technique makes use of a laser source, a beam splitter, and two photodetectors. It involves mixing the incoming quantum state with a strong, locally generated coherent state on a beamsplitter and measuring the interference pattern between the two. The result of the measurement is proportional to the quadrature of the incoming state, either the amplitude (x) or the phase (p). The homodyne detection method can be seen as the CV equivalent of the polarization measurements performed in discrete-variable (DV) quantum systems,
The laser source emits a continuous-wave (CW) field, which is split into two parts by a beam splitter. One part is used as a local oscillator, while the other part is sent over a communication channel to the receiver. The signal is then mixed with the local oscillator on a beam splitter, and the resulting interference pattern is detected by photodetectors. The photodetectors measure the amplitude and phase of the interference pattern, which can be used to reconstruct the signal.
Homodyne detection is preferred over photon counting in CV-QKD protocols because it provides more information about the signal. Photon counting provides only binary information about the presence or absence of a photon, while homodyne detection provides continuous information about the amplitude and phase of the signal. This allows for a more accurate reconstruction of the signal, which can be used to detect the presence of an eavesdropper.
In addition, homodyne detection is also more tolerant to noise in the system, as it is based on the measurement of the mean value of the signal, rather than the number of photons. This makes it more reliable in real-world applications, where the communication channel is often noisy.
b) Discrete Modulation Protocols
In discrete modulation protocols, signals are made up of a strong phase reference and a weak coherent state. The relative optical phase between the reference pulse and the weak coherent state is set to either 0 or π, effectively encoding the signal onto the weak coherent state. The strong phase reference can be generated using phase-locked lasers located at the sender and receiver. The receiver can perform homodyne or heterodyne detection, with homodyne detection involving a random selection of one of the two relevant quadratures for measurement and heterodyne detection involving the measurement of both quadratures. The security of the discrete modulation protocols is based on the non-orthogonal signal states represented by the weak signal pulses.
Studies have shown that discrete modulation protocols are more robust against excess noise and can achieve longer distances compared to Gaussian modulation protocols. These protocols have been shown to be compatible with efficient error-correction procedures and to provide unconditional security against arbitrary collective attacks using decoy states. The key rates attainable by discrete modulation protocols are higher over significantly longer distances compared to Gaussian modulation protocols.
Quadratures are mathematical representations of a physical signal in terms of amplitude and phase. In the context of quantum physics and quantum key distribution (QKD), quadratures refer to the two components of an optical signal that can be measured: the amplitude quadrature (x) and the phase quadrature (p). These two quadratures can be thought of as equivalent to the real and imaginary parts of a complex number, respectively.
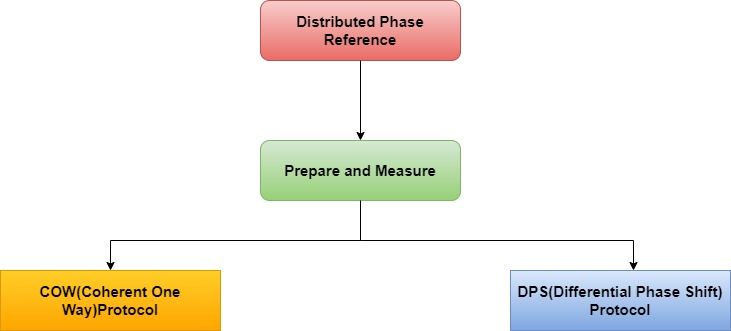
3) Distributed Phase Reference Protocols (DPR)
The Distributed Phase Reference (DPR) protocols have been attracting attention due to their simple implementation with current technology. These protocols utilize the properties of coherent states to monitor the quantum channel and maintain the phase coherence of the pulses.
The two main protocols in this category are the Differential Phase Shift (DPS) and Coherent One way (COW) protocols. The sender modulates the phases of the equal intensity coherent states in the DPS protocol, while a common phase is shared by all the pulses in the COW protocol, but they differ in their intensities.
i) Prepare and Measure
a) COW(Coherent One Way)Protocol
The Coherent One-Way (COW) Quantum Key Distribution (QKD) protocol is a secure method for transmitting information using quantum mechanics. The protocol is a variant of the distributed-phase-reference protocol, which uses weak coherent pulses to represent the information being transmitted.
In the COW protocol, two time-bins are used to represent 0 and 1. In the first time-bin, 0 is represented by a vacuum state followed by a coherent state. In the second time-bin, 1 is represented by a coherent state followed by a vacuum state. These two states can be differentiated based on the arrival time of each state, which allows for accurate information transmission.
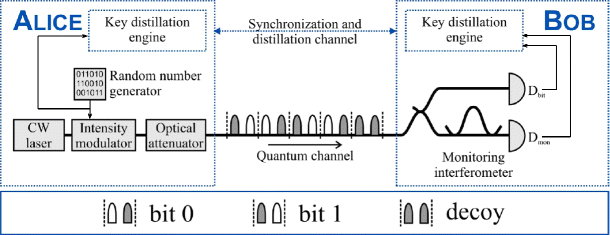
In addition to these two states, the protocol also includes a third state known as the decoy sequence. This state randomly prepares weak coherent pulses in both time-bins and is used to monitor the channel for eavesdropping and other disturbances.
The coherence between two non-empty, successive time-bins is used to monitor the channel for eavesdropping and other disturbances. A fiber interferometer is used to measure the coherence and visibility, which helps to ensure the security of the information being transmitted.
The COW protocol offers several advantages over other QKD protocols. For example, it does not require polarization control and can be implemented with only two detectors. Additionally, the protocol allows for a completely submissive receiver, making it easier to use.
The first implementation of the COW protocol was done in 2005 and in 2015, a system implementing the protocol was reported to have a record distance of 307 km.
b)DPS(Differential Phase Shift) Protocol
In the DPS-QKD configuration, a single photon is divided into N(≥ 3) time slots with equal period T at Alice’s site. The keys are encoded by preparing the relative phase shift between consecutive pulses in 0 or π randomly. Bob detects the incoming photon using an interferometer setup with a path time delay difference equal to the period T.
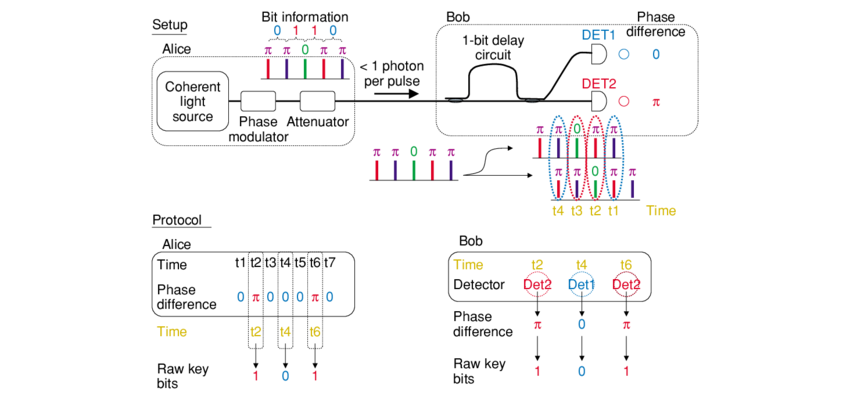
Here is an example of DPS-QKD protocol using single photons by taking the example at N = 3.The detection at Bob’s site occurs in four possible time instances:
(a) a photon in the first period passes through the short path;
(b) a photon in the first period passes through the long path and a photon in the second period passes through the short path;
(c) a photon in the second period passes through the long path and a photon in the third period passes through the short path;
(d) a photon in the third period passes through the long path. Two detectors (D1 and D2) at the output ports of Bob’s interferometer clicks for 0 or π phase difference based on Alice’s modulation. Once a photon is detected, Bob records the time and which detector clicks.
If the detectors click at the (b) or (c) time instances, Bob tells Alice only the information of time instances through a classical channel; otherwise, Bob discards the photon. Using the time-instance information and her phase encoding records, Alice knows which detector clicked at Bob’s site.
Defining the clicks at D1 and D2 as “0” and “1” respectively, Alice and Bob can obtain a confidential bit string as a sharing key.
The photon sent from Alice to Bob is one of the following states (|100⟩±|010⟩±|001⟩)/sqrt(3) [from left to right 1,2,3 represents the photon at each time slots).
As these are nonorthogonal with each other, the four states cannot be perfectly identified by a single measurement based on noncloning theorem, which guarantees the security of the scheme.